LDAP (Lightweight Directory Access Protocol) and Kubernetes are two critical technologies often used in enterprise environments. LDAP helps manage user data, while Kubernetes handles container orchestration. Integrating LDAP with Kubernetes is crucial for enhancing security and streamlining access control in your cluster. This article will explain how to set up and manage LDAP groups within a Kubernetes cluster, providing step-by-step guidance and practical insights.
Setting Up Your LDAP Directory
Before integrating LDAP with Kubernetes, you need a well-organized LDAP directory. This directory stores user and group data and serves as the foundation for access management.
An LDAP directory consists of hierarchical entries like users, groups, and organizational units. Ensure your directory is populated with accurate user and group data. Use tools like OpenLDAP or Microsoft Active Directory to set up your LDAP directory. Proper planning here will prevent issues later when integrating with Kubernetes.
Connecting LDAP to Kubernetes
Connecting LDAP to Kubernetes is essential for centralized authentication and access control. Kubernetes can leverage LDAP for user authentication, enabling streamlined management of access permissions across clusters.
Start by configuring your Kubernetes API server to use an LDAP-based identity provider. You’ll need the LDAP server’s URL, binding credentials, and base DN (Distinguished Name). Once configured, Kubernetes can authenticate users against the LDAP directory, making it easier to manage permissions centrally.
Configuring Access Permissions
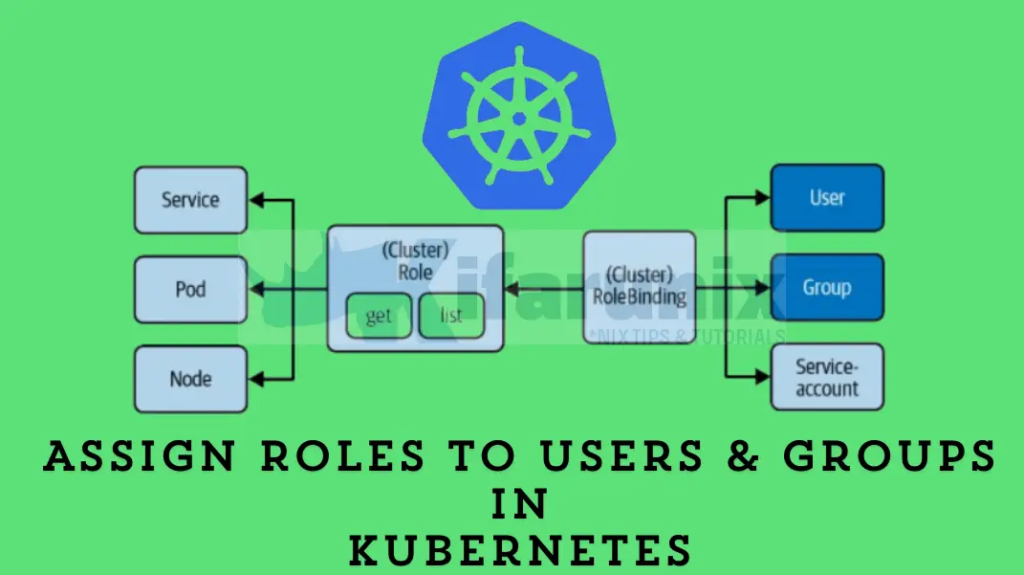
Access permissions in Kubernetes define what resources users and groups can interact with. By integrating LDAP, you can map existing LDAP groups to Kubernetes roles and role bindings.
- Role Mapping: Assign specific permissions to LDAP groups using Kubernetes role definitions.
- Role Bindings: Link LDAP groups to roles within specific namespaces or across the cluster.
Testing the Integration
After configuring permissions, test the integration to ensure that users in specific LDAP groups have the correct access rights. Use tools like kubectl auth can-i to verify permissions for different users.
Maintaining the System
Regularly audit your LDAP directory and Kubernetes role bindings. Ensure that only authorized users have access to critical resources. Periodic maintenance helps prevent security breaches.
What Is an LDAP Group in Kubernetes?
An LDAP group in Kubernetes represents a collection of users managed through LDAP. These groups are mapped to roles or role bindings in Kubernetes, controlling access to resources.
For instance, an LDAP group called dev-team can be granted access to the development namespace. This simplifies managing permissions since you control access at the group level rather than individually.
Why Do You Need LDAP Groups in Kubernetes?
LDAP groups in Kubernetes provide centralized user management, enhancing security and efficiency. Instead of managing permissions for individual users, you can define roles for groups, making it easier to scale access controls as your team grows.
LDAP groups also improve compliance by enabling granular control over resource access. For example, you can restrict production access to a specific LDAP group, ensuring that only authorized personnel can deploy changes.
How to Set Up LDAP Integration with Kubernetes
Setting up LDAP integration involves configuring the Kubernetes cluster to recognize and authenticate users from an LDAP directory. Follow these steps to establish a seamless connection:
- Prepare the LDAP Server: Ensure your LDAP server is running and accessible. Populate it with users and groups that will need access to Kubernetes.
- Install the Required Plugins: Some Kubernetes distributions require additional plugins or tools to enable LDAP authentication. For example, the Dex Identity Provider is commonly used to integrate LDAP with Kubernetes.
- Modify the API Server Configurations: Update your Kubernetes API server to include LDAP authentication settings. This involves adding flags like –oidc-issuer-url and –oidc-client-id.
Install the Necessary Tools
Integrating LDAP with Kubernetes requires specific tools. These tools help bridge the gap between your LDAP directory and the Kubernetes cluster.
- OpenLDAP or Active Directory: As the LDAP server.
- Dex or Keycloak: This is used to enable OIDC (OpenID Connect)-based authentication.
- kubectl: This is used to query and manage Kubernetes clusters.
Configure the LDAP Connector
The LDAP connector handles communication between the LDAP server and Kubernetes. Configure the connector with details like the LDAP server’s URL, base DN, and binding credentials.
Test Your LDAP Integration
Before going live, test the integration thoroughly. Ensure that LDAP users can log in to Kubernetes and access only the resources assigned to their groups.
Retrieving an LDAP Group in Kubernetes
To retrieve an LDAP group in Kubernetes, use the LDAP connector’s search functionality. Alternatively, query the LDAP directory directly using tools like ldapsearch.
Use Kubectl to Query LDAP Groups
With the integration in place, you can use Kubectl to query LDAP groups and verify their role bindings. For example:
bash
Copy code
kubectl describes role binding <rolebinding-name>
This command displays which LDAP groups are linked to specific roles, helping you confirm that permissions are correctly assigned.
The Bottom Line
Integrating LDAP with Kubernetes is essential for managing access in large-scale environments. By connecting LDAP groups to Kubernetes roles, you can centralize authentication, enhance security, and streamline user management. Follow the steps outlined in this guide to set up and manage LDAP groups effectively within your Kubernetes cluster. Regular testing and maintenance will ensure your system remains secure and efficient.